We are thrilled to announce that the new StackHawk code scanning integration with GitHub is live! 🎉
If you are a developer that has been integrating security testing into your GitHub pipeline, you are probably familiar with GitHub code scanning and the related integrations.
If you aren’t then here is the tl;dr:
GitHub has been beefing up the security testing capabilities that can be deployed natively in its pipelines. GitHub first did this with the source code analysis (SCA) tool Dependabot, and more recently rolled out code scanning with the static analysis tool CodeQL.
The latest addition to GitHub’s security testing capabilities has been third-party code scanning integrations. With these third-party integrations, developers can add a much wider range of security tools to their existing CI pipelines for more comprehensive security testing.
StackHawk Integrates Dynamic API and Application Security Testing in GitHub Code Scanning
Integrating security testing into the developer experience is at the heart of what we are doing at StackHawk – which is why we are beyond excited to roll out our GitHub code scanning integration.
By using the StackHawk code scanning integration in GitHub, developers can run application and API security testing whenever they check-in code. And, they are notified about new findings immediately in the GitHub security tab.
StackHawk is the first and only dynamic application and API security testing (DAST) tool to integrate with GitHub code scanning. As a DAST scanner, StackHawk tests a running version of your application to identify potential security vulnerabilities - like those found in the OWASP Top 10 and the OWASP API Top 10. DAST invokes an app or API the same way an attacker would, helping teams find vulnerabilities before they are in the wild.
But unlike traditional DAST tools that scan an app after it is in prod, the new StackHawk code scanning integration means critical security information and alerts live right in the repo.
For developers this means shortening the feedback cycle and making secure code delivery fast. Devs can test on every push, get notified immediately when a vulnerability is introduced, remediate on the spot, and get back to feature development.
Get Going with StackHawk’s Code Scanning Integration
This getting started guide assumes that you have already configured your app in the StackHawk UI and have access to your StackHawk API key.
If you still need to stand up your app in StackHawk, check out our getting started docs and then meet us back here.
📺 Watch & Learn
Watch our video detailing the ins and outs of our code scanning integration here.
Code Scanning Configuration
To get going with the StackHawk code scanning integration from GitHub, navigate to the security tab of your GitHub repo. Once there select code scanning alerts.
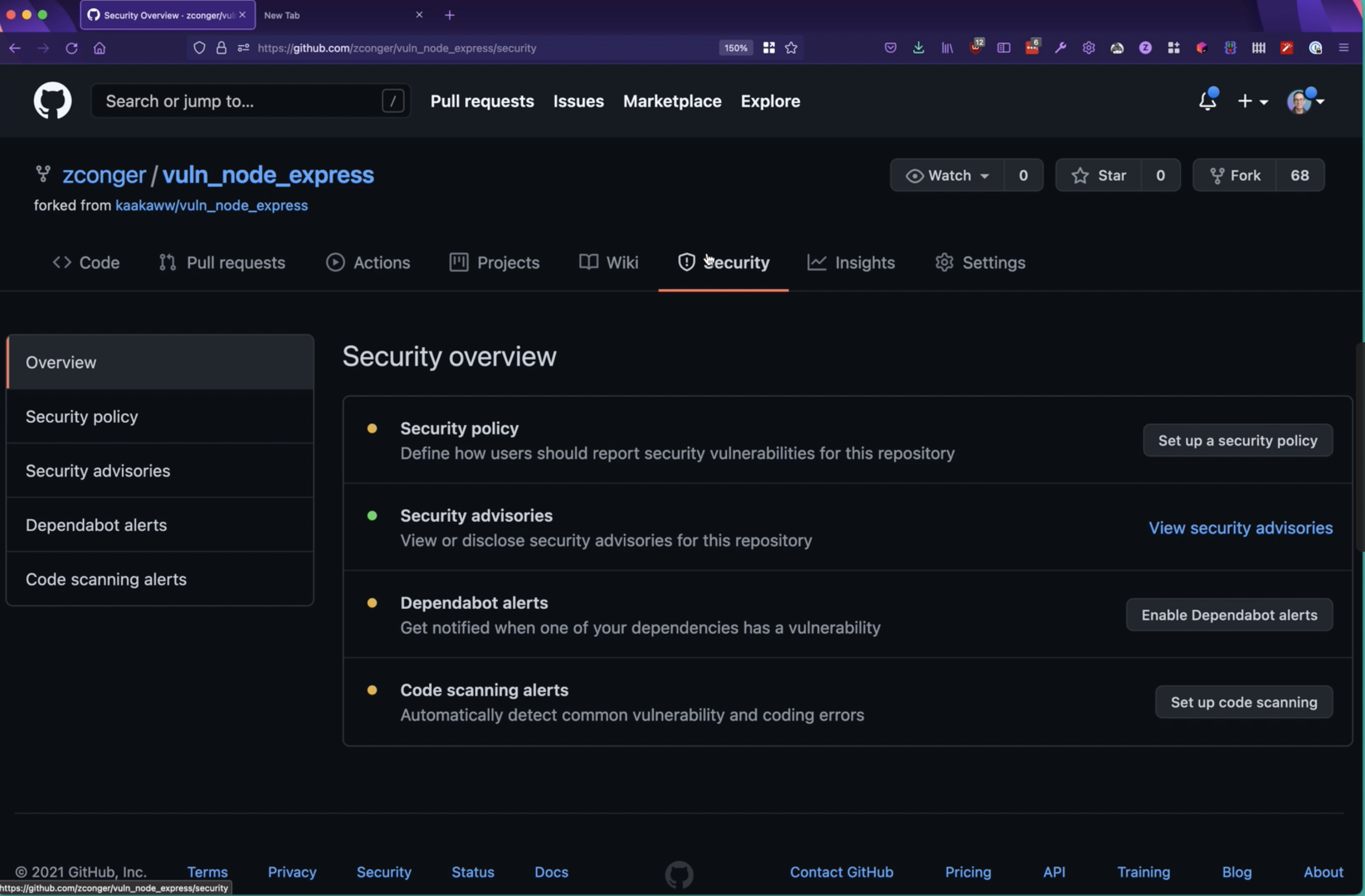
Next, navigate through the list of integration partners and select StackHawk to begin setting up your code scanning workflow.
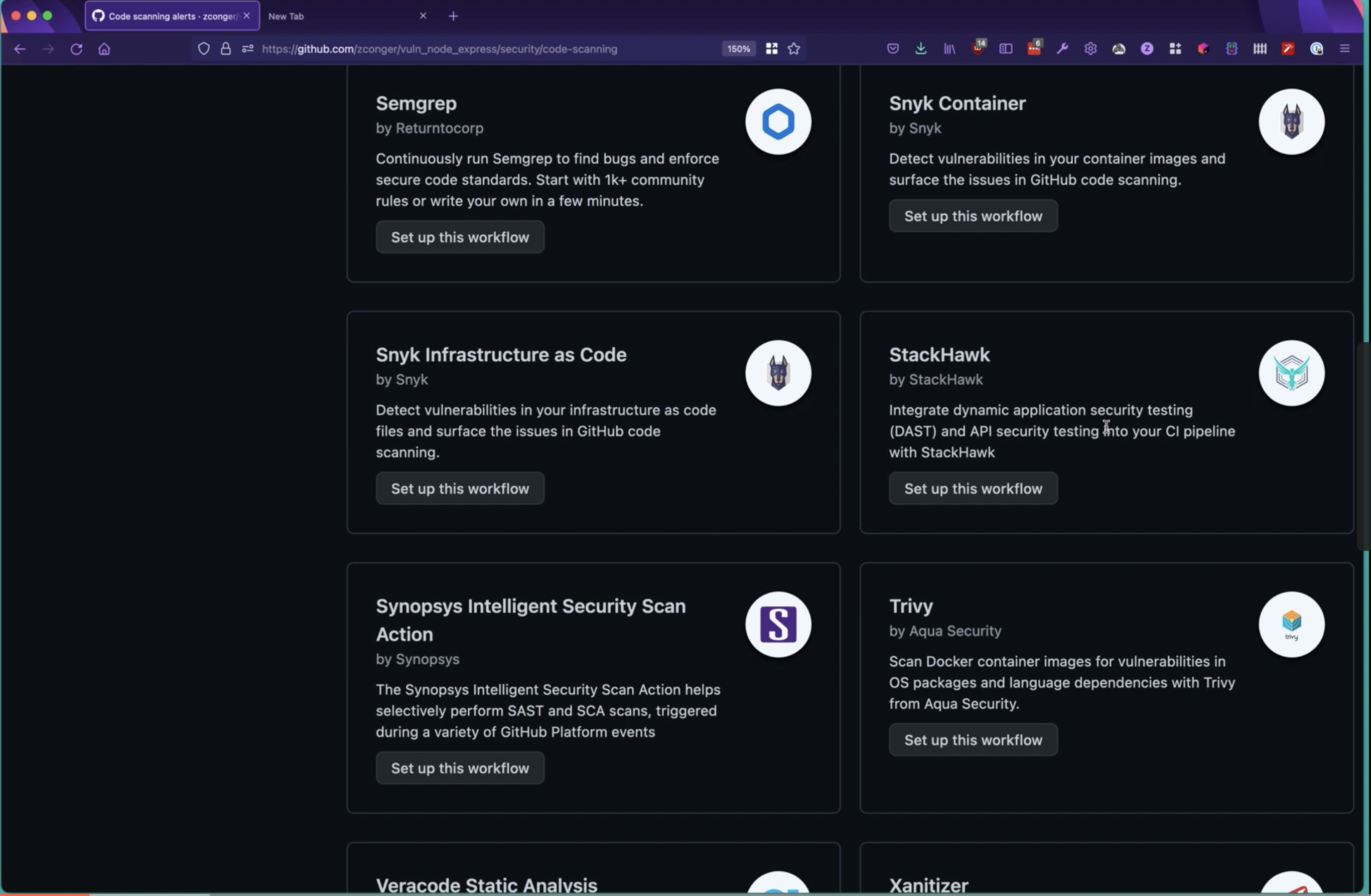
From there, you will automatically be prompted to set-up a new GitHub Actions workflow configuration file that will be added to your existing repo.
In the new workflow, you will need to update two steps:
The command to start your service or app.
If you would like the build to continue on errors. You can either set this to
trueorfalse.
StackHawk YAML Configuration
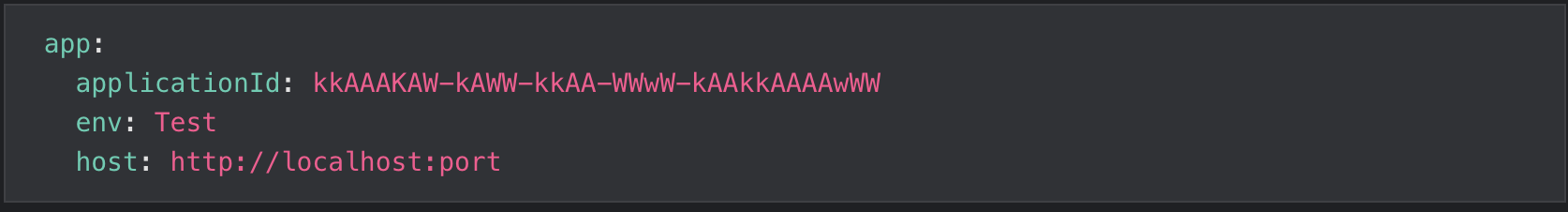
Once you have finished setting up your code scanning workflow, you will need to add the StackHawk YAML to the base of your repo. This file will consist of three mandatory elements, all of which can be found in the StackHawk platform.
Your application ID
Your app’s environment
The host your app is running on
Outside of the required fields, StackHawk allows for significant customization for your application. For more information, check out our docs or reach out to our support team.
If you also enable the app.failureThreshold setting in your StackHawk configuration file (stackhawk.yml), then you will receive notification through the GitHub Security tab if a scan has found issues that meet or exceed that threshold. Accepted values are related to finding severity so this field can be set to high, medium, or low.
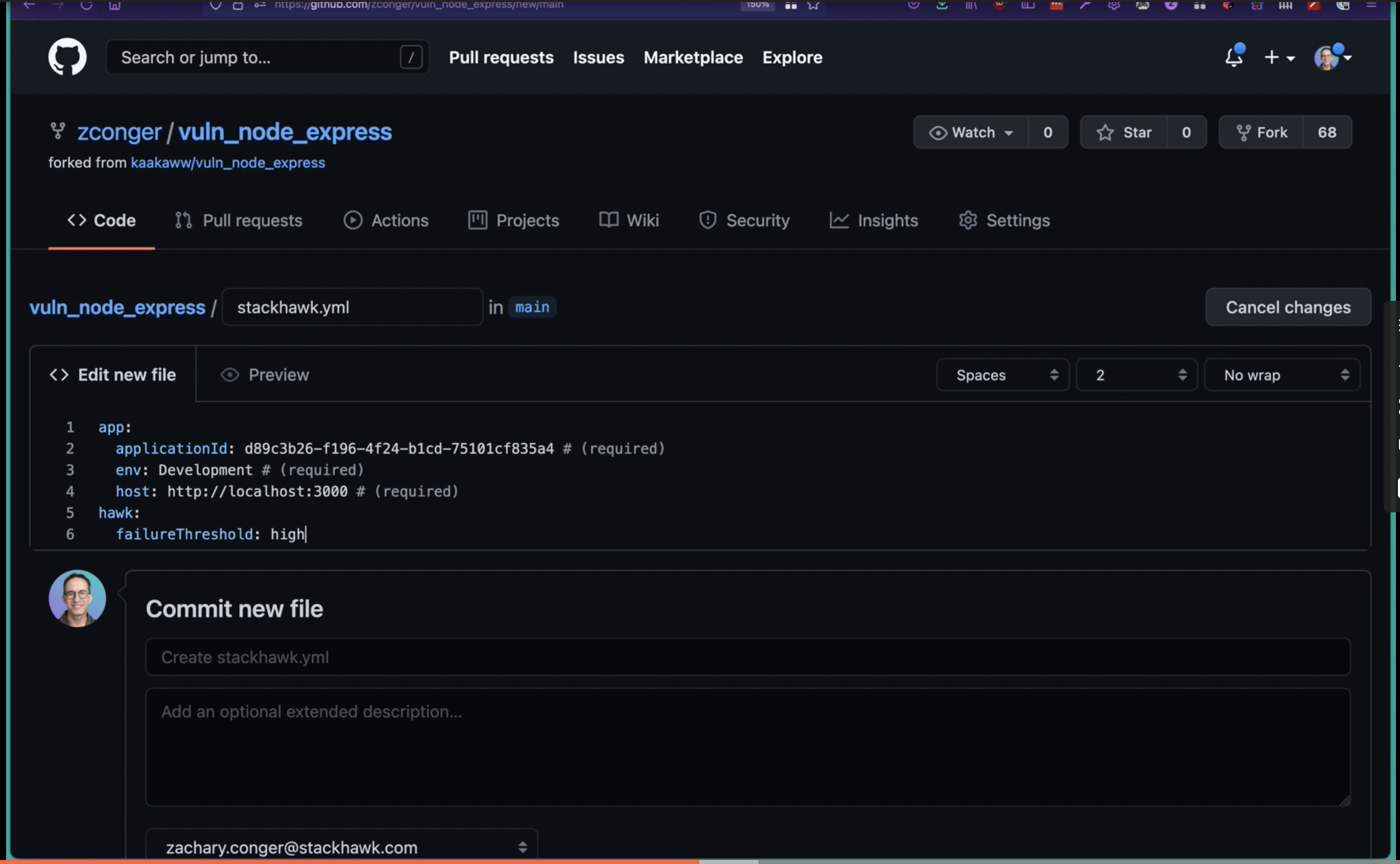
Commit your StackHawk YAML to your repo.
Storing Your StackHawk API Key
To execute a scan in GitHub, you will also need to store your StackHawk API key in GitHub. Fortunately, GitHub makes this super easy with their secrets management tooling.
Grab your API key out of the StackHawk platform, and then click the settings tab in your repo.
Navigate down to secrets and create a new secret with the name HAWK_API_KEY and paste in your API key value.
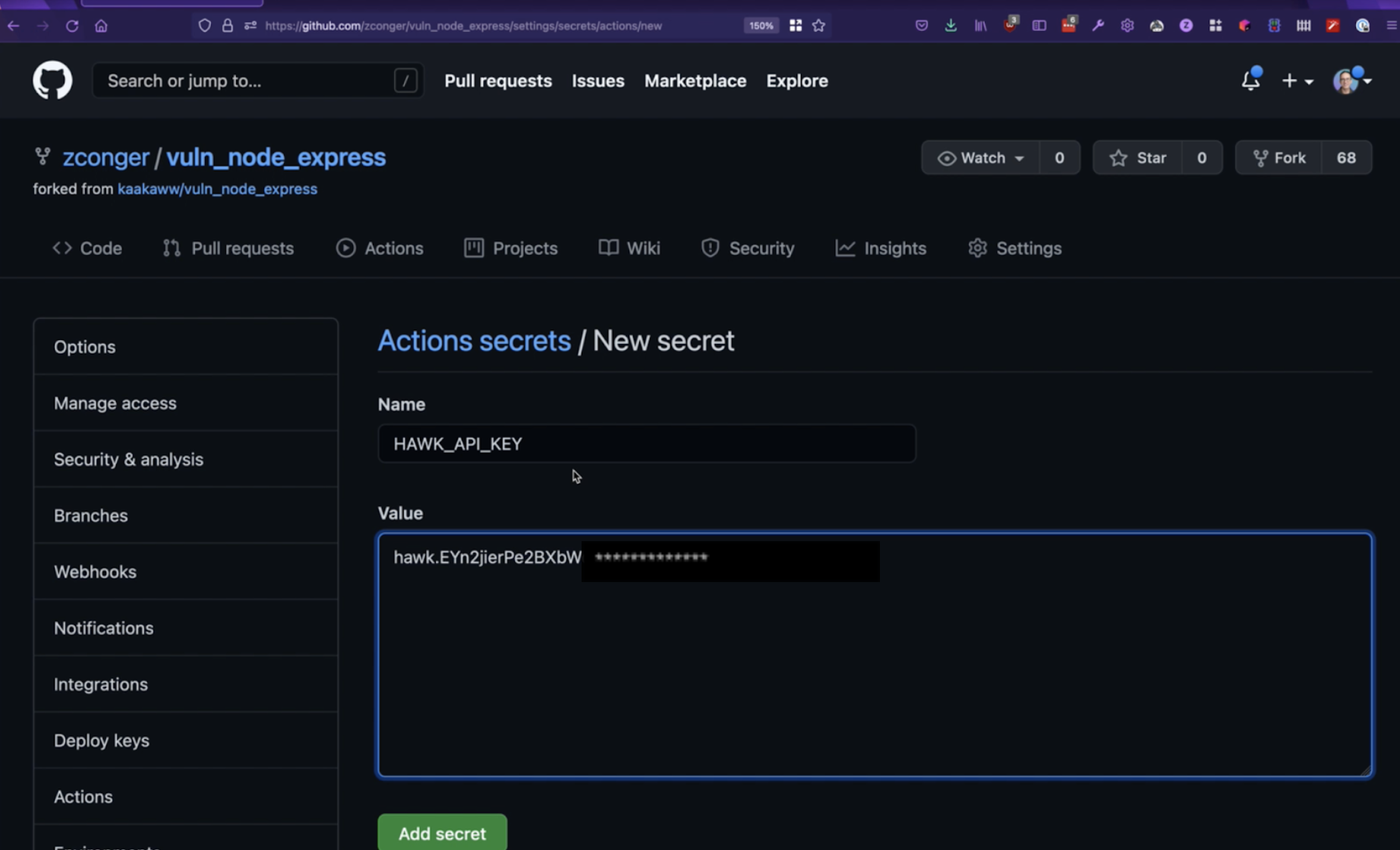
If you don’t know your StackHawk API key, you can generate a new one by clicking on your username in the bottom left of the StackHawk UI and navigating to settings.
Running Code Scan
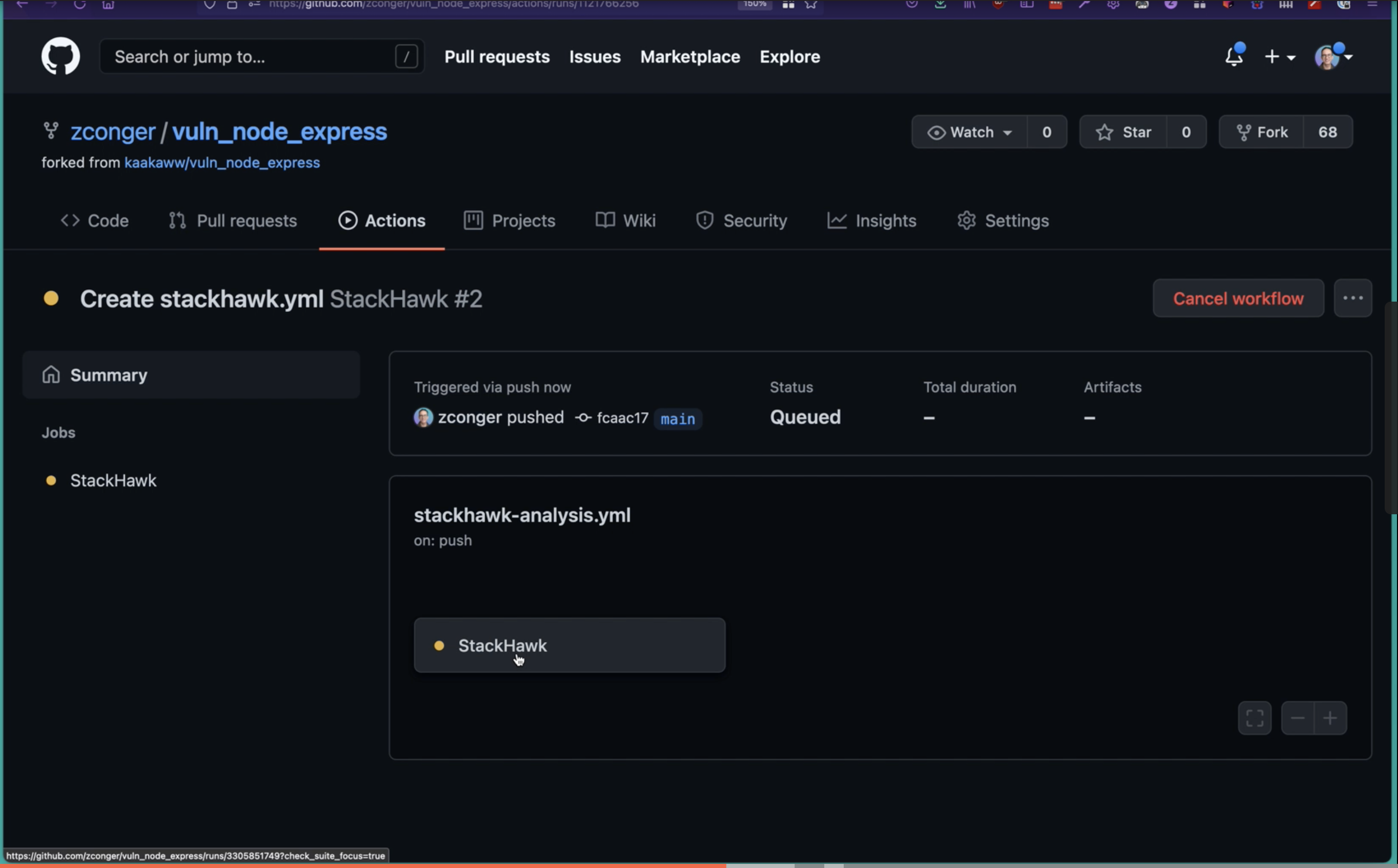
The hard work is behind us! Now it is time to start running StackHawk’s code scanning integration.
By default, StackHawk will run every time you check-in code. After you have pushed your code, navigate to the Actions tab and you should see StackHawk running.
If you have configured a failure threshold in StackHawk, you will get notifications in the security tab when findings meet or exceed your threshold. The findings will create a badge on the security tab, which you can click into for more details.
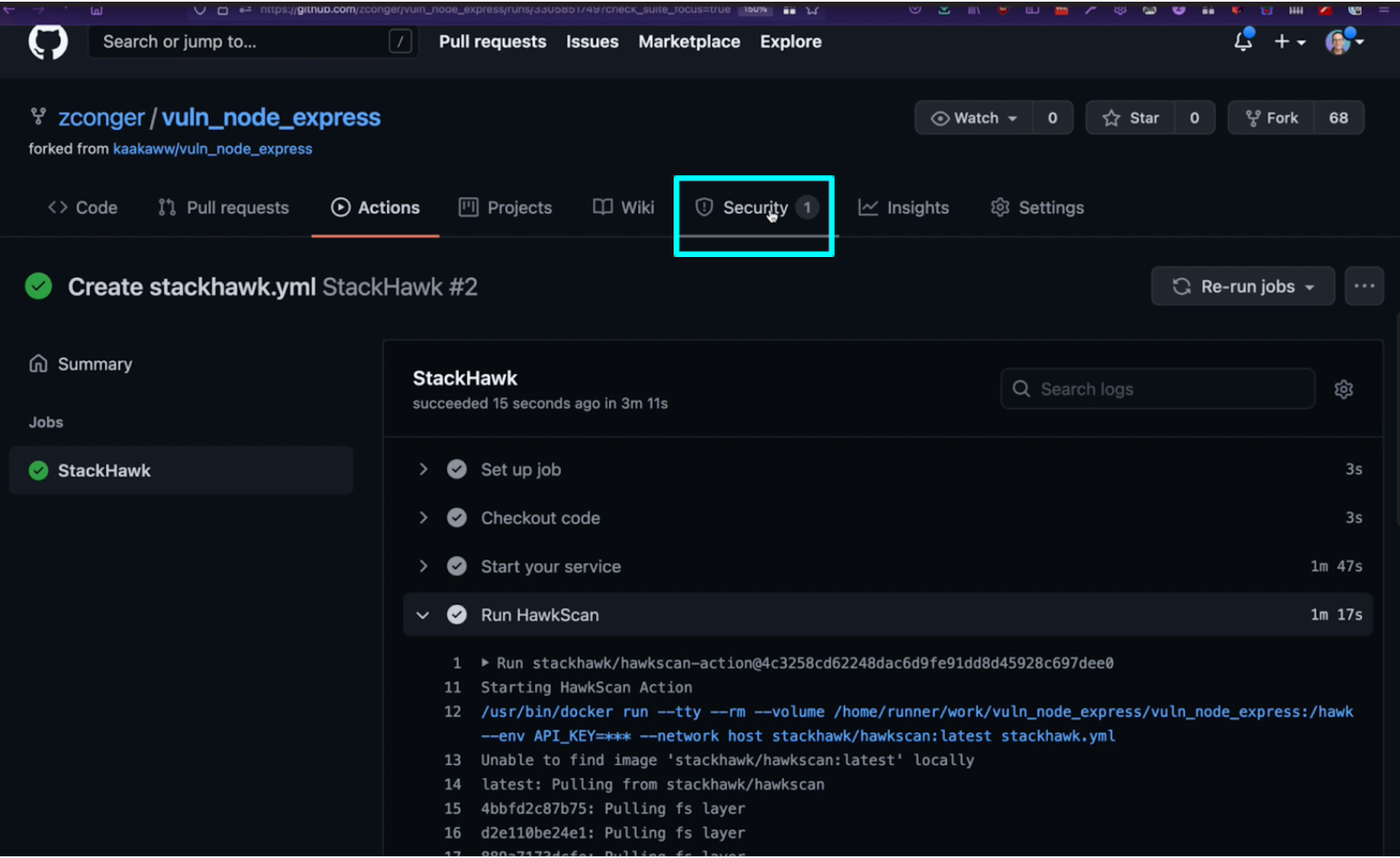
Once you click into the code scanning alert, you will be able to navigate to the scan results in the StackHawk UI with a single click.
In the StackHawk platform, users can triage alerts to allow future builds to pass.
Conclusion
Getting notified when a new security vulnerability is introduced doesn’t have to take tons of tooling, platforms, and overhead. The new StackHawk code scanning integration in GitHub meets developers where they are already working so they can find API and application security vulnerabilities quickly and easily. Configuration is dev-friendly and relies on two YAMLs and a few clicks in the GitHub UI.
From there, testing runs seamlessly when you check-in code. Developers get notified right away when a vulnerability is introduced so they can quickly remediate, and they can have confidence the code they are shipping is secure.
So login to GitHub and get going!



