On this Valentine’s day, make sure to pop open a bottle of champagne and drink it with the one you love. And by the one you love, I mean your API. And by drink champagne, I mean scan every pull request with HawkScan to make sure it is free of any vulnerabilities.
At StackHawk, we love APIs:, GraphQL, SOAP and our own REST API that supports our platform. And we make sure to regularly scan them all.
StackHawk loves REST and GraphQL and SOAP
For our true blue and stalwart suitor (the simple API backed by a DB setup) we can two-step with them at the local sock hop (what’s a two-step and sock hop? who are these references even intended for?). Scanning a GraphQL app with HawkScan in Kubernetes is a snap. Just throw your sweetheart (HawkScan) in your sidecar (your sidecar is a Kubernetes sidecar but also works as a metaphor) and drive (probably to the local malt shop or something).
Here’s an example of our manifest.
apiVersion: v1
kind: Pod
spec:
volumes:
- name: conf-dir
configMap:
name: configuration-dir
- name: script-authentication-dir
configMap:
name: configuration-script-authentication
containers:
- name: hawkscan
image: stackhawk/hawkscan:latest
- name: API_KEY
value: hawk.xxxxxxx.xx
- name: APPLICATION_ID
value: xXXxxxX-xxxx-xxxx-xxxx-XxXxXX
- name: REPO_DIR
value: /conf
volumeMounts:
- name: conf-dir
mountPath: /conf
- name: script-authentication-dir
mountPath: /conf/scripts/authentication
- name: vulny-app
image: my-vulny-app/vuln-graphql-apiWe’ve loaded our stackhawk.yml and custom authentication scripts in our /conf directory that we’ve volume mounted onto our pod with a config map. We use this setup against GraphQL, SOAP and REST.
We test each release of HawkScan against our vulny apps (look them up here and pick your poison https://github.com/kaakaww) to ensure it catches all the vulnerabilities (security exploit vulnerabilities not ones related to emotional maturity).
But what happens when your application doesn't look like a single container and looks more like this.
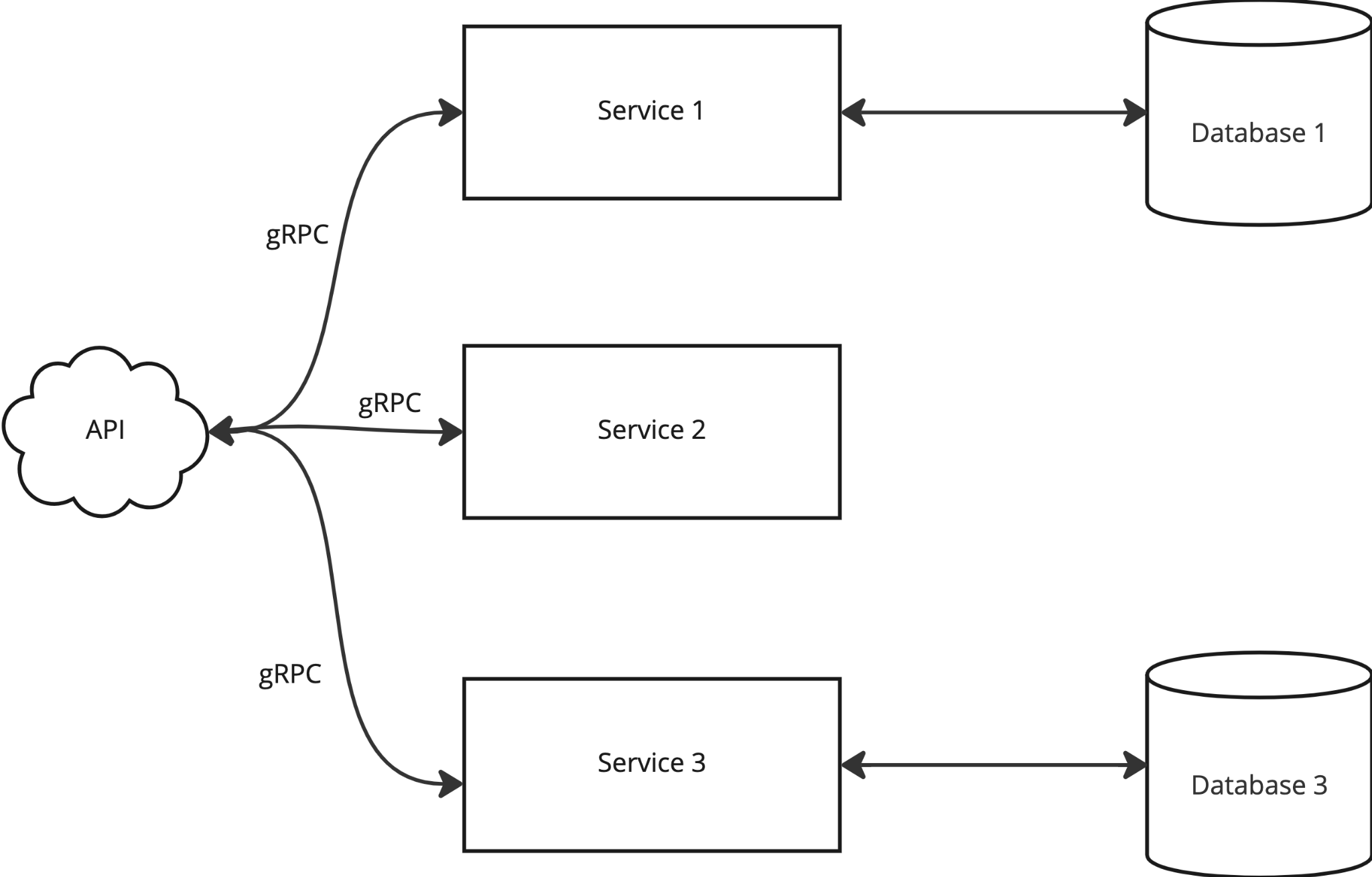
On top of that, you made a great choice to run gRPC, but you can't HawkScan gRPC.
We look like this too
To avoid corrupting staging and production data, we create an environment to test against a PR, as ephemeral as a kiss blown in the wind. Our traditional REST API is backed by microservices with gRPC communication. So to get meaningful scan results from our scanner we need all those microservices and their supporting databases (hopefully with some data) running.
We heart Docker
On each PR, we launch our API and every one of its dependencies in Docker containers and scan it. And if you’re using GitHub Actions you can throw HawkScan Action into your pipeline…look at how cute she is: https://github.com/stackhawk/hawkscan-action. Just a few lines of configurations in your workflow brings it in:
- name: RunHawkScan
id: run-hawkscan
uses: stackhawk/hawkscan-action@main
with:
apiKey: ${{secrets.HAWK_API_KEY}}
So we spin up each of our services in their own Docker container and our API and scan them with our HawkScanner. But that’s a lot of containers…I don’t know about you but the majority of our gRPC services are backed by databases. So we’re spinning up at least two containers for each service and that’s a lot of containers…well at least 2 times the amount of containers as before.
But we’ve had our eye on Kubernetes, he’s cute
We could just as easily spin up a bunch of pods in Kubernetes with all their dependencies and launch HawkScan as a job or pod to scan the service.
apiVersion: batch/v1
kind: Job
spec:
spec:
volumes:
- name: conf-dir
configMap:
name: configuration-dir
containers:
- name: hawkscan
image: stackhawk/hawkscan
volumeMounts:
- name: conf-dir
mountPath: /confThis feels like scanning a monolith. Don’t we love microservices and tiny testing and shifting left? I want to get back to our true blue suitor.
Our Dance Card is Not Full
But wouldn’t it just be easier and more in line with engineering best practices to scan each microservice? Yeah, we see you and we’re here for you. HawkScan is starting a beta program for scanning gRPC services, so now you can stand up each microservice on its own and scan directly, making gRPC a first-class citizen like REST, SOAP and GraphQL.
So, if you heart gRPC like we do, enroll in our gRPC scanning beta and we can all go off holding hands and skipping through the tulips.
We heart you (sign up for our gRPC beta)
Roses are red
Violets are blue
Our API is secure
How bout you(rs)?
Dana White is Senior Software Engineer at StackHawk
Read more
Sign up for a free trial of StackHawk today
Get Started (Documentation)




