Security Testing for the
Modern Engineering Team
Focused on pre-production API and web application security testing, StackHawk gives Development teams the ability to actively run security testing as part of their traditional software testing workflows, while giving AppSec teams the peace of mind of controlled and security tested applications in production.
DAST Reinvented for modern teams
that deploy software everyday.
Find.
Triage.
Fix.
FIND
Security testing is Software testing.
StackHawk works where and how you work to find security bugs; from testing locally to reviewing PRs and even breaking the build to ensure your code is secure before it hits production, and without slowing down your development teams.
Easily Configure as Code
Run in ANY CI/CD
Run in the CLI
Test ANY API
Optimized Scanner

Utilize Existing tools
Custom Scripts & Data
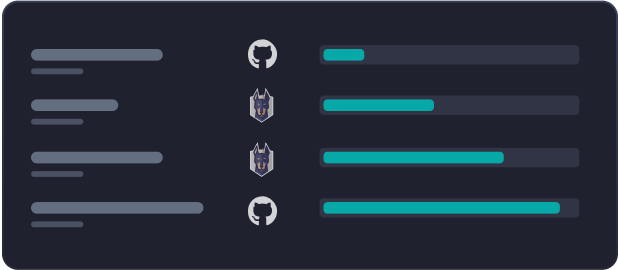
Surface on every PR

Sign Up
for your Free
Account Today!
TRIAGE
Trust AND Verify.
StackHawk helps scale AppSec, by empowering developers to take ownership of their security bugs. Surfacing security bugs in their native development environments, allows developers to quickly identify, prioritize, and investigate security issues.
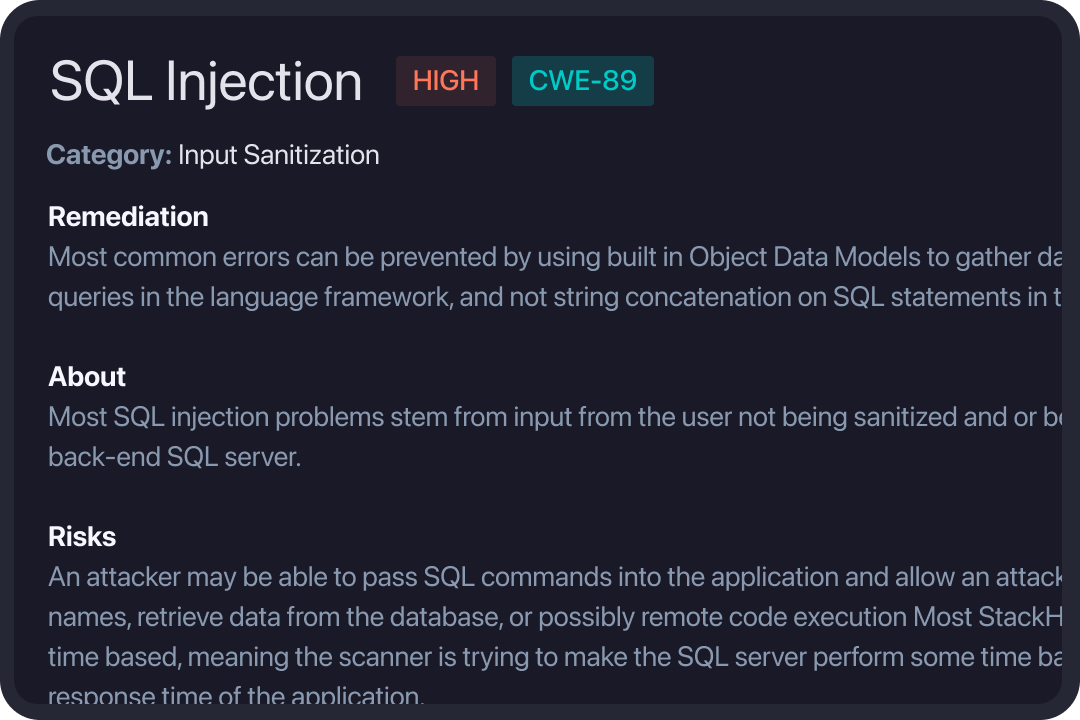
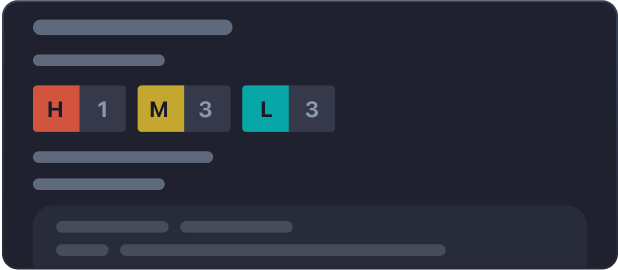
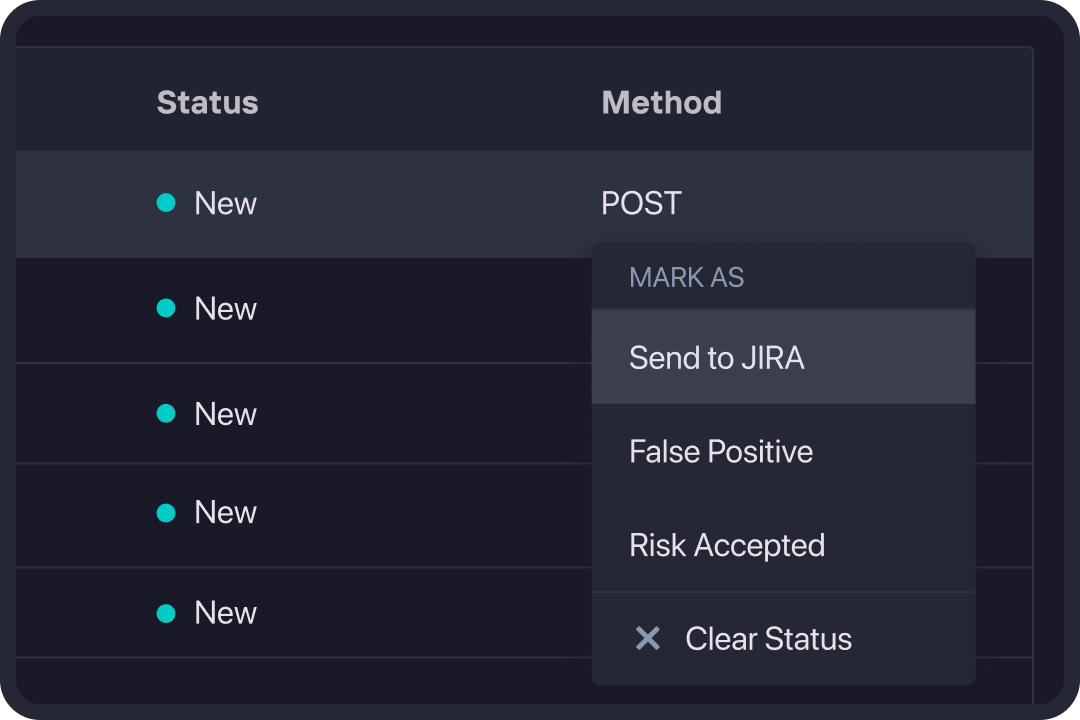
Prioritize Results
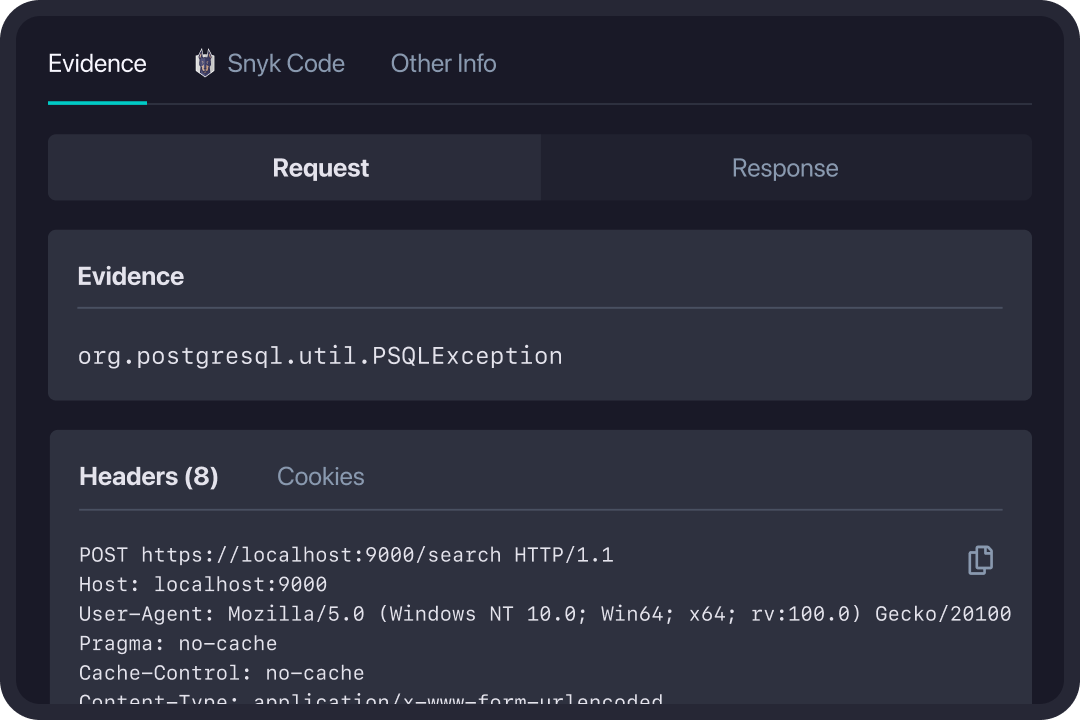
Investigate & Collaborate
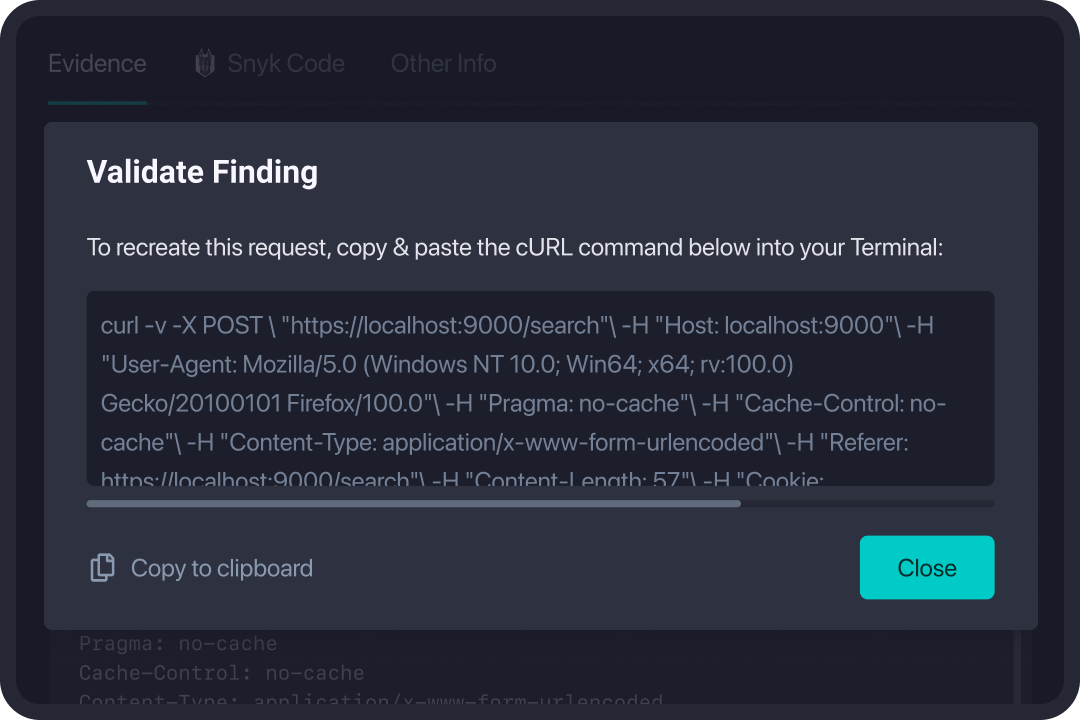
Validate Findings
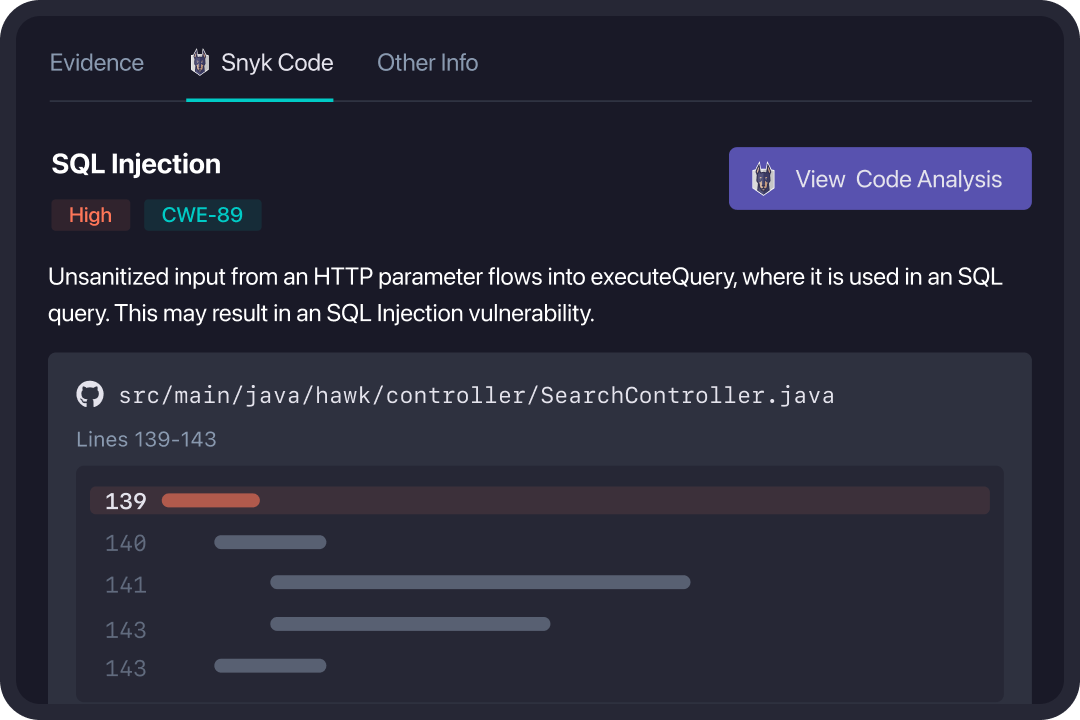
Correlate DAST & SAST Results
Manage Risk

On Every PR
Review scan results along with a summary of potential vulnerabilities directly in your GitHub pull request.
FIX
Streamline security testing &
fix security bugs in pre-production

StackHawk is the only API and web app security testing solution built for engineers to own the initial triage and fix of security issues from within their CI/CD workflows.
Eliminate
Disruption
Iterative
Testing
Actually
FIX
Ship Safer
Code Faster


Sign Up
for your Free
Account Today!
Get Hands-On Experience
Give Us A Test Drive!
Take control of your AppSec program with StackHawk. Discover, Test, and gain Continuous Oversight. Get started!
